
WELCOME TO
PHANTOM.OS

Synchronization
Absence of synchronization with corporate servers
Personalization
Inability to establish connections between Phantom users
Tracking
Absence of GSM pinging capability for the subscriber
Access
Control over all permissions is available only to the user
Applications
Specialized applications not available to the general public
GPS coordinates
Simulation of virtual coordinates for all Phantom subscribers
PHANTOM OS - THE KEY TO SECURE COMMUNICATION
01.
Our team has implemented a set of technical and virtualized security solutions preinstalled on the mobile device to maintain the full anonymity of its owner.
02.
We have created a unique environment that does not collect user data and cannot send information to third-party services or agencies. Everything the user does on a Phantom device remains known only to the user.
03.
All services that usually have hidden access to all user data on a device (images, contacts, browser history, phone microphone, camera, etc.), as well as those that analyze conversations and create a “Consumer Profile” of the user, do not operate on Phantom.

COMPLETE ANONYMITY
IN CALLS AND
MESSAGING
Phantom is based on a proprietary operating system, which is an analogue of the well-known "ANDROID". In the system, access to the user’s personal data by installed applications is eliminated. Phantom uses only its own application package.
1
APPLICATION LAUNCH WITH THE USER’S PRIOR PERMISSION;
2
EMERGENCY RESET OF THE PHONE TO A CLEAN OPERATING SYSTEM STATE;
3
PHONE RESET AFTER SEVERAL INCORRECT PIN CODE ATTEMPTS;
4
AUTOMATIC RESET OF THE PHONE IN CASE OF PROLONGED INACTIVITY;


SIMULATION OF GSM IDENTIFIERS
From the mobile operator we get only internet access by blocking the GSM module, leaving access solely for
mobile data
consumption. - no calls/SMS.

ENCRYPTED
CALLS
Standard cellular communication is unavailable on Phantom. All calls take place within the network between subscribers. For calls to cellular numbers, number spoofing is used.

INTEGRATION OF PROPRIETARY VPN
We created our own
VPN service for subscribers. Our
VPN servers are
private and keep
no logs of any
subscriber
activity.

MESSENGER FOR COMMUNICATION
Phantom anonymous messenger, available
only to users
of our operating system. All chats and
file exchanges
are accessible
only to you.

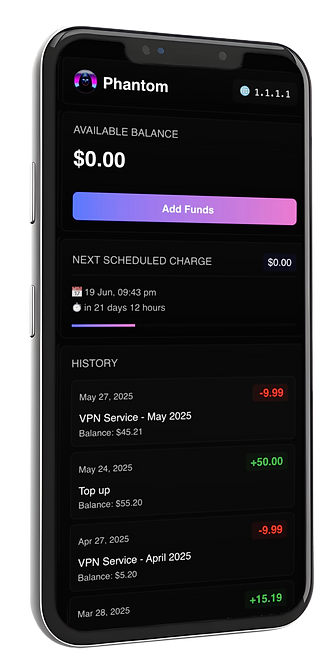
INDIVIDUAL PAYMENT METHOD
For the comfort and convenience of
our users, we
developed an individual anonymous payment system for monthly subscriptions or internal plans.



DIGITAL FINGERPRINT
NO COLLECTION
OF PERSONAL
DATA
When speaking with clients, we often encounter the widespread misconception that you can buy a phone with
an IMEI of 000000000 or a separate “work phone” and then forget about anonymity issues.
1. Zero IMEI
Frankly, this is a marketing myth.
Phones with a zero IMEI code raise many suspicions and questions with the mobile operator when registering on a cellular tower. Direct access to the subscriber’s conversations is not encrypted. The mobile operator records that the subscriber lacks an IMEI identifier and adds them to a "Suspicious Activity" list.
2. “Work phone”
In reality, this is a common misconception.
With phones bought “for work,” it gets even more interesting. Every second, each smartphone sends your personal data to corporations like Apple or Google, as well as to every developer of the apps installed on your phone. At times, certain services can activate the camera, microphone, and other device functions without the user’s knowledge or consent.
Phantom devices have eliminated the possibility of collecting subscriber data and do not allow the installation of programs or applications that include personal data collection options or requests for access to other phone functions.


PHANTOM FUNCTIONAL APPLICATION PACKAGE
Technical solutions for your security and anonymity
Phantom Messenger
for internal communication

Phantom – anonymous cryptocurrency payment

Phantom Caller – anonymous
calls within and outside network

Phantom VPN – anonymous service without log records

Threema Messenger – alt communication channel

Telegram Messenger – for usual business use

PRICE OF
PHANTOM PHONES
Variants of devices for personal and commercial use
Phantom LITE
550$ / 1 device
Google Pixel 6 series / 128 GB / 6 RAM
Plan: STANDART
Available:
✔Phantom OS operating system;
✔Full package of Phantom applications;
✔Emergency phone formatting;
✔Unlimited calls within the Phantom network;
✔Encrypted devices in the network;
✔GSM block & GPS spoofing;
✔Anonymous browser;
Phantom PRO
1000$ / 1 device
Google Pixel 8 series / 128 GB / 8 RAM
Plan: STANDART
Available:
✔Phantom OS operating system;
✔Full package of Phantom applications;
✔Emergency phone formatting;
✔Unlimited calls within the Phantom network;
✔Encrypted devices in the network;
✔GSM block & GPS spoofing;
✔Anonymous browser;
✔ Incoming GSM calls to your Phantom;
Phantom Business
4800$ / 10 devices
Google Pixel 6 series / 128 GB / 6 RAM
Plan: Optimal
Available:
✔Phantom OS operating system;
✔Full package of Phantom applications;
✔Emergency phone formatting;
✔Unlimited calls within the Phantom network;
✔Encrypted devices in the network;
✔GSM block & GPS spoofing;
✔Anonymous browser;
✔ Incoming GSM calls to your Phantom;
✔ Dedicated Phantom network;

PHANTOM PREMIUM
PLANS DETAILS
We support the operation of unique, individual user anonymization networks that require regular maintenance.

FAQ
(Frequently Asked Questions)
01.
How to use Phantom correctly?
A common mistake users make is using Phantom near their personal phone. We recommend communicating via secure connection while keeping all other devices at a distance of 8–10 meters during the conversation.
02.
What should I do if I don’t understand how to use the device?
Our team provides full instructions for the devices and software. Also, in case of individual or emergency situations, every client can contact our technical support. The support contact is preinstalled in all messengers on the device by default.
03.
How to install additional applications on Phantom?
Phantom devices support only their own software or applications that do not require access to the phone’s hardware-information services. You can send your request or suggestion to our technical support, and we will assess the feasibility of installing a particular application on your Phantom or offer an alternative. Installation files will also be provided by our team.
04.
Do you have other phone models available?
We regularly improve and adapt our software for more modern and up-to-date types of devices. Through testing, we select only those gadget models that have no “gray areas” or other unforeseen risks for our subscribers. When placing an order to purchase Phantom, you can check the available device models with our managers.